Lightweight Directory Access Protocol LDAP authentication modes include anonymous simple and SASL authentication modes. I do not have much experience using kerberos.
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
The following procedure is a summary of the Kerberos authentication algorithm.
. WinRM cannot process the request. To add this principal in qshell you should type the following. SASL is extensible and lets you use a wide variety of protection methods.
Kerberos Authentication Explained. Open Registry Editor regedit as the user you run the EMC. Connect and share knowledge within a single location that is structured and easy to search.
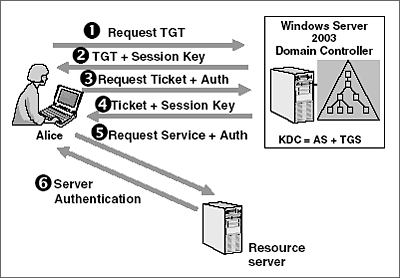
According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld. The TGT validates the user identity and is good for a specific ticket granting server. If so the reason Kerberos authentication fails is because the authentication request is sent using the FQDN of the CAS array which does not match the SPN.
-Kerberos accepts domain user names but not local user names. When using an HTTP server that is listening on a port other than the standard port of 80 the Kerberos principal needs to have this as part of the host name. Kerberos works as follows.
-The user name or password specified are invalid. When using Kerberos authentication which of the following terms is used to describe the token that verifies the identity of the user to the target system. Internet Explorer determines an SPN by using the URL thats entered into the address bar.
The SPN is passed through a Security Support Provider Interface SSPI API InitializeSecurityContext to the system component thats in charge of Windows security the Local Security Authority. In classic Kerberos users share a secret password with a Key Distribution Center KDC. Possible causes are.
Authentication is mutual so client and server authenticate at the same steps and they are both sure they are communicating with the right counterpart. 26 rows When using Kerberos authentication which of the following terms is used to describe the token. According to my understanding there is some negotiation between the client and server following the following steps here get-requests.
Passwords are never sent across the network because only keys are sent in an encrypted form. -Kerberos accepts domain user names but not local user names. -The Service Principal Name SPN for the remote computer name and port does not exist.
Kerberos uses a trust broker model and symmetric cryptography to provide authentication and authorization of users and systems on the network. Geturl - returning a WWW-Authenticate. Kerberos header telling this authmethod is supported.
Close all MMCEMC instances before proceeding. When using Kerberos authentication which of the following terms is used to describe the token that verifies the identity of the user to the target system. When using Kerberos authentication which of the following terms is used to describe the token that verifies the identity of the user to the target system.
In the modern world MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. The principal advantages in adopting Kerberos as an authentication service are. - Routers send routing information only to their neighbor routers.
EXPLANATION Choose SASL Simple Authentication and Security Layer authentication mode to use Kerberos with LDAP. The authentication server validates the user identity and grants a ticket granting ticket TGT. However please check if the following steps can solve your issue.
-Kerberos is used when no authentication method and no user name are specified. NIST SP 800-95 from IETF RFC 1501 A widely used authentication protocol developed at MIT. -Kerberos is used when no authentication method and no user name are specified.
-The Service Principal Name SPN for the remote computer name and port does not exist. The entire routing table is sent to other routers. Which of the following authentication methods uses tickets to provide single sign-on.
The client sends an authentication request to the authentication server. The following error occurred while using Kerberos authentication cannot find the computer. Resolving The Problem.
Hes a big 3 headed dog with a snake for a tail and a really bad temper. Which of the following are required when implementing Kerberos for authentication and authorization. The only thin I need to pass is a username no password is needed.
Kerberos a network authentication protocol included in the Microsoft Windows operating systems can be used in conjunction with Security Support Provider Interface SSPI to provide pass-through authentication with secret key.
Five Steps To Using The Kerberos Protocol
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
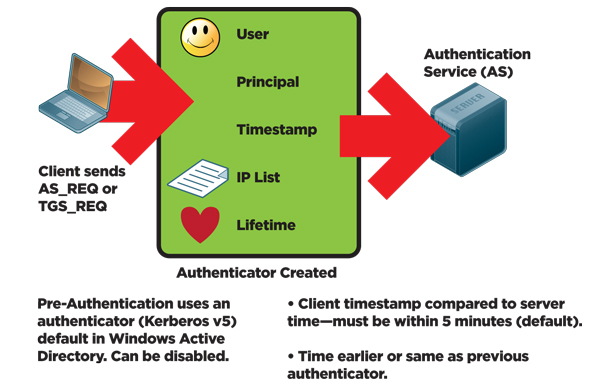
0 Comments